Security at Universal Foundry
We understand the importance of security in today’s digital landscape and have taken extensive measures to safeguard our infrastructure and services. This document takes an in-depth look at the security measures and protocols we have implemented to ensure the highest level of protection for our platform and your data. We believe in transparency and want our users to understand how seriously we take their security.
Universal Foundry is hosted in Amazon Web Services (AWS). We detail how we use AWS services in more detail below. For more details on the steps AWS takes to secure their infrastructure as part of the shared-responsibility model see their AWS Whitepapers and Guides.
Introduction to Universal Foundry
We provide infrastructure and tools to make the development experience in Unreal Engine faster and more reliable.
Our Security Guiding Principals
- Data is always encrypted in transit over public networks and at rest.
- Customer data and secrets is encrypted at rest with a encryption key unique to the organization.
- Least privilege is used when granting access to all users and services.
Key Terminology and Features
Horde
Horde is a set of services provided developed by Epic. Universal Foundry manages Horde and its supporting services on your behalf.
Horde features currently supported by Universal Foundry:
- Build Automation (CI/CD)
- Test Automation
- UnrealGameSync Metadata Server
Horde features coming soon:
- Remote Execution
- Studio Analytics
- Mobile/Console Device Manager
- Cloud Distributed Data Cache (DDC)
Horde Dashboard
The Horde Dashboard is a single page web application (SPA). The dashboard’s public assets are hosted behind an Amazon Cloudfront hosted CDN. It is accessed from a web browser using HTTPS (TLS v1.2 or v1.3).
Horde Coordinator and API
The Horde Coordinator provides API services externally to the Horde Dashboard as well as internally to Horde Agents. An independent deployment of Horde Coordinators is run for every organization. All access to the Horde API is encrypted via TLS (v1.2 or v1.3), TLS is terminated via an AWS load balancer.
Internet-facing access to the Horde API, as used by the Dashboard, requires a valid Universal Foundry session.
Internal-facing access to the Horde API is controlled via AWS Security Groups and is limited to the Horde Agents running for your organization.
The Horde Coordinator uses the following to maintain state and coordinate agents:
- Amazon DocumentDB
- Redis (via ElastiCache)
- S3
- Elastic File System
Horde Agent
The Horde Agent is software running on an Amazon EC2 that communicates the the Horde Coordinator and orchestrates work to be done.
Universal Foundry currently supports running the Horde Agent on x86-64 platforms with Windows Server 2022 and Ubuntu 2024.04.
The EC2 instance backing a Horde Agent is never reused by another organization.
Horde Agent Pools
Horde Agent Pools are a group of Horde Agents that share configuration and a data cache. An organization may have several agent pools with different environment variables, EC2 instance types, and operating systems.
Horde Data Cache
The Horde Data Cache consists of two parts:
- An S3 bucket used by both the Horde Coordinator and Horde Agents to share data across builds.
- An EBS volume or snapshot per agent used to cache the agent’s workspace and build intermediates.
UnrealGameSync Metadata Server
Horde provides an UnrealGameSync metadata server. Please contact Universal Foundry if you’d like to enable this feature for your organization.
Universal Foundry Dashboard
The Universal Foundry Dashboard is a server-rendered web application used to grant Universal Foundry sessions and well as configure the Universal Foundry platform. It is accessed from a web browser using HTTPS (TLS v1.2 or v1.3).
Examples include:
- Configuring Horde Agent Pools
- Updating secrets
- Performing group management for users
Build Artifacts
Builds artifacts are the outputs of producing builds in Horde. Build artifacts include many types of data including:
- Logs, stored in S3.
- Packaged Unreal Engine builds, typically stored in S3 or pushed to an external system.
- UnrealGameSync binaries, pushed back into your Perforce stream.
- Docker images, pushed to your configured image registry.
Customer Provided Secrets
Customer provided secrets are stored in AWS Secrets Manager and DynamoDB.
Secrets are always encrypted in transit and at rest, and at rest encryption is performed using an AWS KMS key that is unique for your organization.
Secrets may also be stored in S3, DocumentDB, EBS, or EFS depending on how they are used by the Universal Foundry platform. When stored in these systems they remain encrypted by your organization’s unique KMS key.
Data Security
Protection of Customer Data
All data submitted to Universal Foundry services by authorized users is considered confidential. All data is encrypted in transit across public networks and encrypted at rest. All build artifacts and organization secrets are encrypted with AWS KMS keys that are unique to each organization.
Additionally, organization data is never co-mingled. All resources that store customer data or secrets are never shared or reused between organizations.
Access Management
Access is controlled based on the principle of least privilege. Universal Foundry employees and services only have the level of access required to perform their job functions and complete specific tasks. We enforce multi-factor authentication, including strong passwords and a secondary factor. Additionally, time-limited federated credentials are used whenever possible.
Universal Foundry limits employee access to administrative roles and privileges. We also apply the principles of least privilege and need to know access to customer data for administrator accounts.
All employee access to production environments and systems is logged using AWS CloudTrail.
Platform and Network Security
Universal Foundry uses our Virtual Private Cloud (VPC) to logically isolate networks. Security groups are used to restrict and isolate networks through ingress and egress rules.
Patch Management
Universal Foundry releases software patches as part of our continuous integration processes. We also routinely update our base machine images used by the agents to ensure that latest patches and Windows Updates are in place.
Change Management
General Agile methods are used to develop our products. Well-defined change management processes and procedures are used to determine when and how changes to production systems and services are made.
Specifically, all production code changes must go through a code-review cycle as well as testing in non-production environments. Platform-level infrastructure changes must also be approved via code-review and are additionally tested and tracked using Terraform Cloud.
FAQs
How does Universal Foundry handle authentication?
Universal Foundry uses Amazon Cognito to provide identity management and user authentication.
This allows Universal Foundry to support multiple authentication schemes:
- username/password
- social logins (like Google Workspace)
- federated SAML provided by an organization
- federated OpenID Connect (OIDC) provided by an organization
See here for more details on how Amazon Cognito handles authentication with a third-party identity provider.
When a user accesses Universal Foundry without a valid session they are redirected to Universal Foundry’s sign in page. This begins an Authorization Code Flow with Proof Key for Code Exchange (PKCE) flow between the Universal Foundry session manager acting as an OIDC relying party (RP) and Amazon Cognito acting as an OpenID Provider (OP). This provides an OAuth 2.0 Access Token that is used to create a user’s session.
For a more detailed overview of OpenID Connect see “What is OpenID Connect”.
A user’s session is then used to provided authorization across the Universal Foundry platform, such as the Universal Foundry Dashboard and the Horde API.
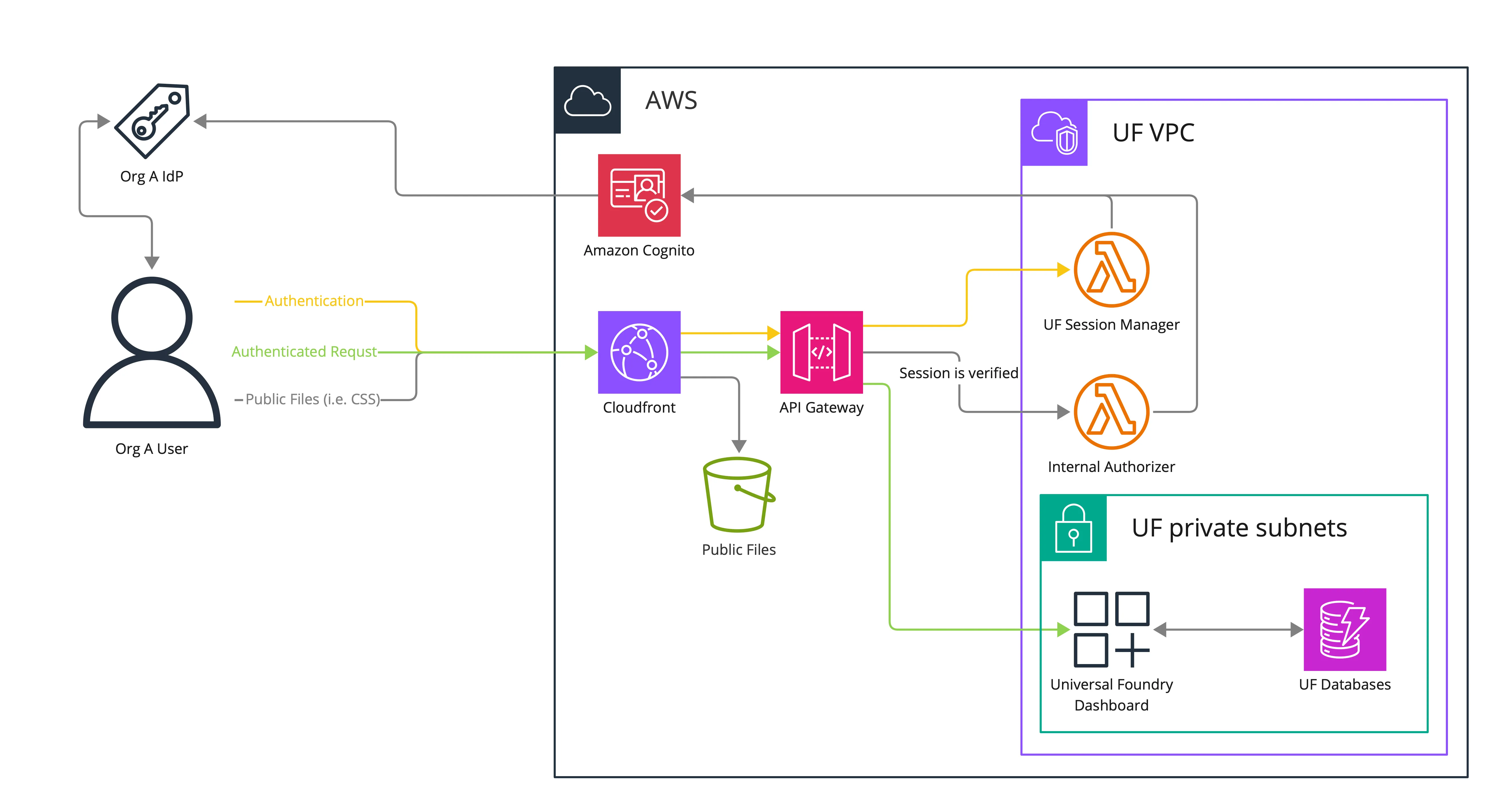
How do users access the Universal Foundry Dashboard?
The Universal Foundry Dashboard is a server-rendered web application. The Universal Foundry Dashboard is accessed from a web browser using HTTPS (TLS v1.2 or v1.3). A valid session is required to access the Universal Foundry Dashboard.
The dashboard is hosted behind an Amazon Cloudfront hosted CDN and an Amazon API Gateway. The Cloudfront CDN is used to serve static public files associated with the dashboard (for example CSS) and otherwise forwards traffic to the API Gateway.
The API Gateway is responsible for verifying that traffic was forwarded from Cloudfront and that a valid user session is present (via a HTTP API Gateway Lambda authorizer).
Based on the result of these checks the user is then either blocked from access, redirected to the login page, or the request is forwarded to the dashboard web server.
The dashboard web server inspects the user’s session to know their identity and handle Universal Foundry dashboard specific authorization.
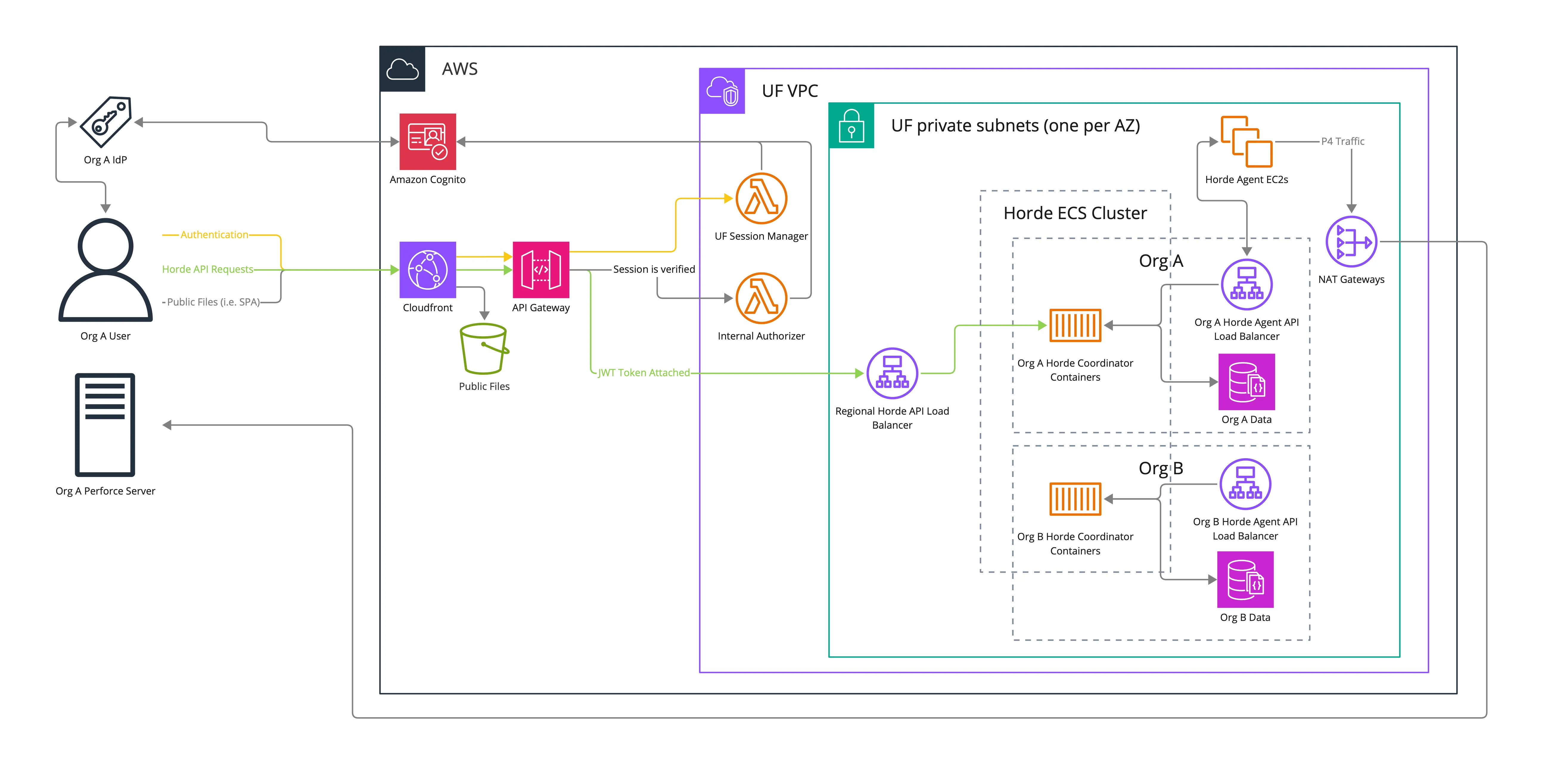
How do users access the Horde Dashboard?
The Horde Dashboard is a single page web application with an API provided by the Horde API. The Horde Dashboard and API are accessed from a web browser using HTTPS (TLS v1.2 or v1.3). A valid session is required to access the Horde API.
The dashboard’s public assets are hosted behind an Amazon Cloudfront hosted CDN.
The Horde API is also hosted behind an Amazon Cloudfront hosted CDN and an Amazon API Gateway. All Horde API traffic is forwarded to the API Gateway by the Cloudfront CDN.
The API Gateway is responsible for verifying that traffic was forwarded from Cloudfront and that a valid user session is present (via a HTTP API Gateway Lambda authorizer). Based on the result of these checks the user is then either blocked from access, redirected to the login page, or the session is inspected to determine the user’s organization and the request is forwarded to that organization’s Horde Coordinator deployment.
When a request is forwarded to the Horde Coordinator a JSON Web Token (JWT) is added to every request. The Horde Coordinator then inspects this JWT to know the user’s identity and handle Horde API specific authorization.
How are Universal Foundry hosted build artifacts accessed?
All Universal Foundry hosted build artifacts are stored in Amazon S3 buckets.
Each bucket:
- is unique per organization
- is encrypted with an organization specific encryption key
- has public access blocks in place
When an artifact is downloaded from the Universal Foundry platform a pre-signed S3 request is generated for the object to be downloaded. This pre-signed URL has a short expiration time; typically 1 minute, the minimum supported by AWS.
How does Universal Foundry access customer-hosted Perforce servers?
Credentials for Perforce servers are stored in AWS Secrets Manager.
The credentials can be changed using the Universal Foundry Dashboard. The Perforce password can only be written using the dashboard, it cannot be read.
The credentials are always encrypted with an organization specific access key and access to the secret is managed by AWS Identity and Access Management. Access to the secret and perforce credentials is only provided to the services that require it, such as the Horde Coordinator. The Horde Coordinator provides Perforce credentials to Horde Agents as needed.
We strongly recommend all Universal Foundry customers implement Helix Server SSL encrypted connections.
All access from Universal Foundry to Perforce servers is from a small number of static IPs.
Key AWS Services used by Universal Foundry
Lambda, ECS and Fargate
Used by the Universal Foundry platform to serve the Universal Foundry Dashboard, handle API requests, and respond to platform events.
EC2
Used by Universal Foundry to host Horde Agents.
Cognito
Identity and access management to allow federated access to Universal Foundry for organizations.
API Gateway
Used by the Universal Foundry platform to manage API mappings and user session requirements to access the Universal Foundry Dashboard and Horde API.
Secrets Manager
Used to hold sensitive platform and organization secrets. All access to secrets is strictly controlled and limited to the resources that need them.